Shared Private State: The HTTPS Moment for Blockchain Technology (Part 1)

The introduction of HTTPS marked a pivotal transformation in internet architecture, enabling secure communication channels that would eventually power the digital economy. Today, web3 stands at a similar threshold with the emergence of shared private state —an advancement that fundamentally alters the scope of what's possible in decentralized systems.
The Public-by-Default Problem
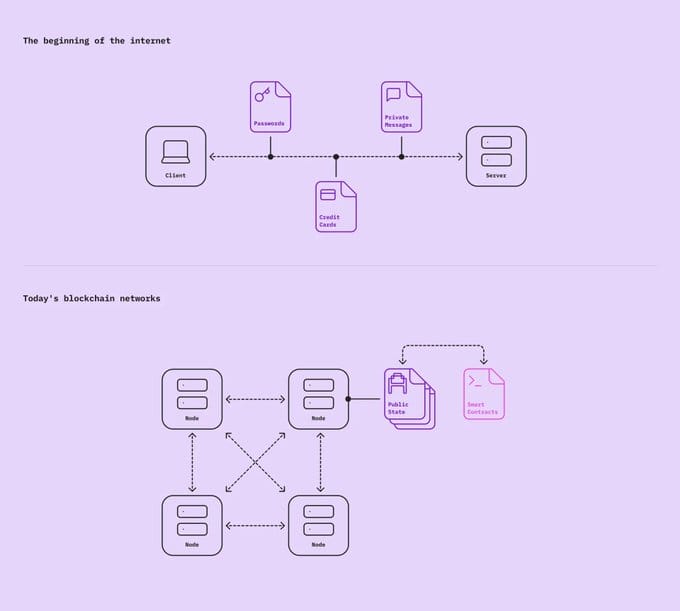
In 1994, sending information over the internet was a risky proposition. Every data packet—whether containing passwords, credit card numbers, or private messages—traveled in plaintext across the network, visible to anyone who cared to look. This fundamental limitation threatened to confine the internet to a mere information-sharing network, rather than the backbone of digital commerce it would become.Today's blockchain networks face a strikingly similar limitation. Every transaction, smart contract interaction, and state change is fully visible to all network participants. This public-by-default architecture creates an insurmountable barrier for many developers looking to build real world applications.
The HTTPS Parallel
HTTPS was perhaps the most consequential transformation in the internet's architecture. By establishing encrypted channels between participants, it enabled secure value exchange while maintaining the network's core properties of openness and verifiability. This shift away from public-by-default unlocked entirely new categories of applications that were previously impossible.
Introducing Shared Private State
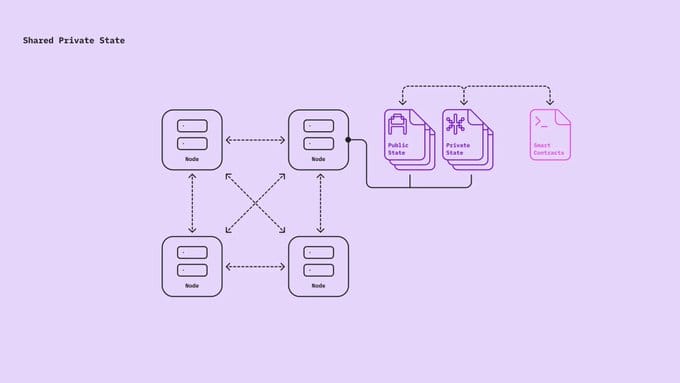
Shared private state promises a similar architectural transformation for blockchain networks. By enabling blockchains to handle any type of data while inheriting the underlying security and verifiability properties of the blockchain, we can unlock an entirely new design space for dApps that was previously impossible.
- Instead of all state being public, applications can maintain encrypted state while preserving verifiability
- Rather than this state existing in isolated silos, encrypted state can be securely used across all protocols and applications
- Where sensitive operations once required trusted intermediaries, they can now be performed directly on encrypted data
This architectural shift enables blockchain applications to handle sensitive real-world data and operations while maintaining the core benefits of decentralization—much like how HTTPS enabled the internet to transform to what it is today while preserving its open nature.
Programmable Cryptography Unlocks Shared Private State

The promise of shared private state is made possible by advancements in cryptographic primitives to unlock what we now refer to as “programmable cryptography”. Much like how public key cryptography enabled HTTPS, recent breakthroughs in programmable cryptography create the foundation for secure computation over encrypted data at scale.Key innovations like Fully Homomorphic Encryption (FHE) enable computation directly on encrypted data, while Secure Multi-Party Computation (MPC) allows multiple parties to jointly compute functions over their private inputs. Trusted Execution Environments (TEEs) provide hardware-backed assurances for secure computation. These primitives, often working in concert, enable a new paradigm where encrypted data can be programmatically shared and computed upon while maintaining cryptographic guarantees.The evolution of these primitives has fundamentally transformed how we think about privacy in blockchain systems. Early privacy solutions like Monero and Zcash used basic cryptographic techniques to shield transaction data, treating privacy as a static property. As zero-knowledge proof systems matured, platforms like Aleo and Aztec emerged, enabling private but isolated state. Now, the convergence of advanced primitives transforms private state from a static concept into a dynamic, composable resource that can be securely utilized across protocols and applications—all while preserving the security properties of the underlying blockchain.
Unlocking Universal Blockchain Programmability
The introduction of shared private state fundamentally changes how developers can approach blockchain applications. Rather than constantly wrestling with the question of what data can safely live on-chain, developers can now build with the same freedom they enjoy in traditional systems:
- Any computation can be performed on-chain while maintaining privacy
- Sensitive business logic can be executed with full blockchain security
- User data can be processed without exposure
- Complex multi-party interactions can happen trustlessly
This removes one of the largest barriers to blockchain adoption: the forced tradeoff between privacy and decentralization. Just as HTTPS enabled developers to build internet applications without constantly worrying about data exposure, shared private state enables blockchain developers to focus on building functionality rather than managing data constraints.
Enabling New Collaboration Models
Shared private state allows blockchain systems to mirror how privacy and transparency work in real-world systems. In traditional finance, for example, market participants maintain selective privacy (protecting their positions and strategies) while still enabling public price discovery and regulatory oversight. With shared private state, DeFi can now implement these same natural privacy boundaries.But the true power lies in going beyond mirroring existing systems. The ability to create collaborative encrypted state with cryptographic guarantees enables multiple parties to work with the same encrypted data, perform verifiable computations on it, and maintain cryptographic proofs of all interactions. This transcends traditional limitations, enabling secure multi-party collaboration without intermediaries and programmable privacy enforced by cryptography rather than policy.
Conclusion
Just as HTTPS was the catalyst that transformed the internet into what it is today, shared encrypted state represents blockchain's transition from experimental technology to practical infrastructure. By removing the fundamental tension between privacy and decentralization, we unlock not just new applications, but entirely new models of collaboration and trust that were previously unimaginable.The future of blockchains isn't just private or public—it's programmably private, where cryptography rather than policy defines the boundaries of what's possible.